You can’t protect what you can’t see.
Aceiss ensures security by delivering unprecedented clarity about user activity across your technology stack.

Aceiss ensures security by delivering unprecedented clarity about user activity across your technology stack.


Reveal hidden information about user accounts, permissions, and activity.
Expose patterns of unauthorized access, anomalous behavior, and dangerous combinations of user privileges.

Integrate with existing access control systems for lasting protection and maximum return on investment.
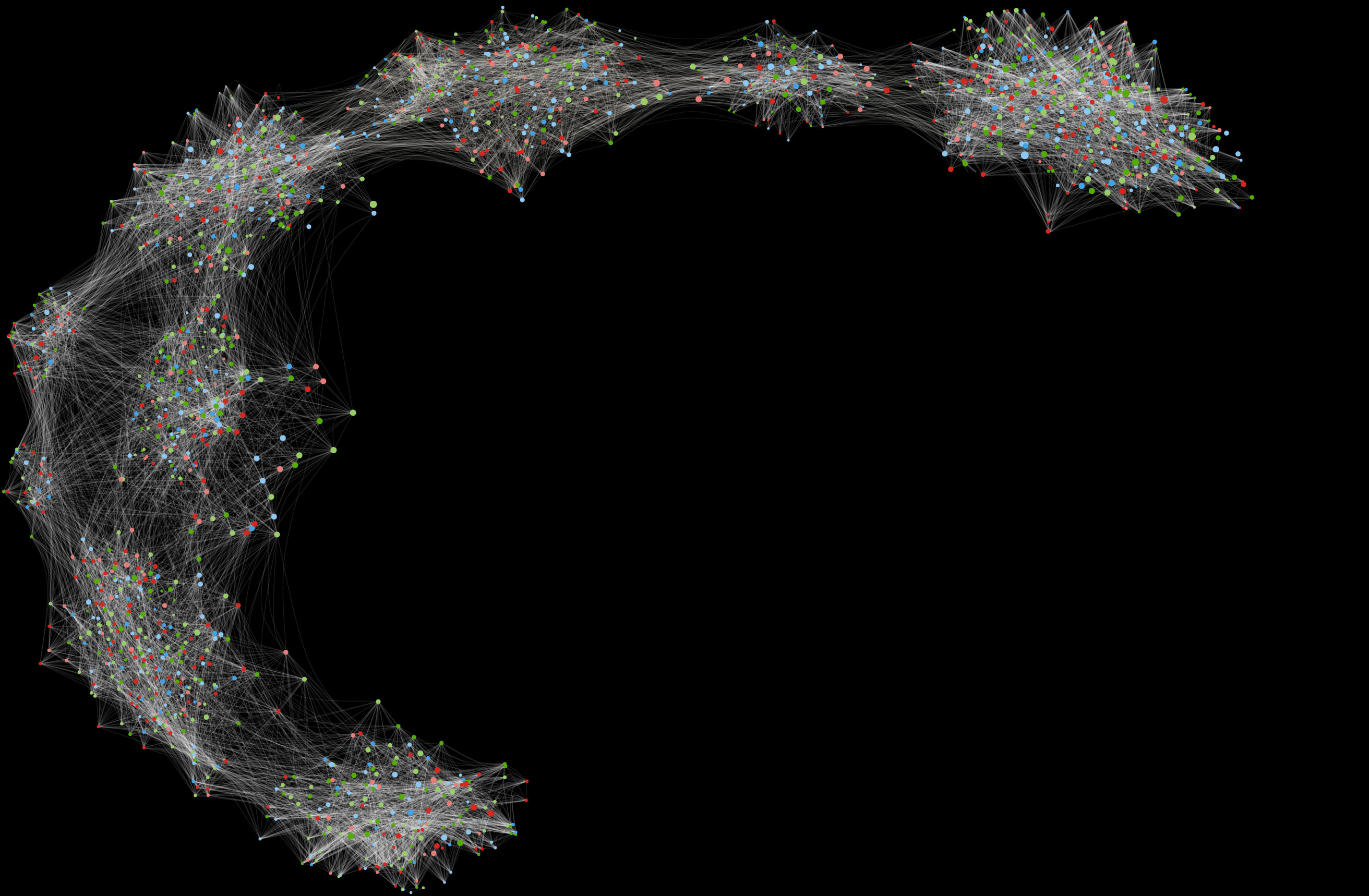
Companies need to quickly shrink their attack surface, reduce implementation costs, and improve security.
Aceiss provides immediate visibility into user access everywhere, regardless of what technologies you use.
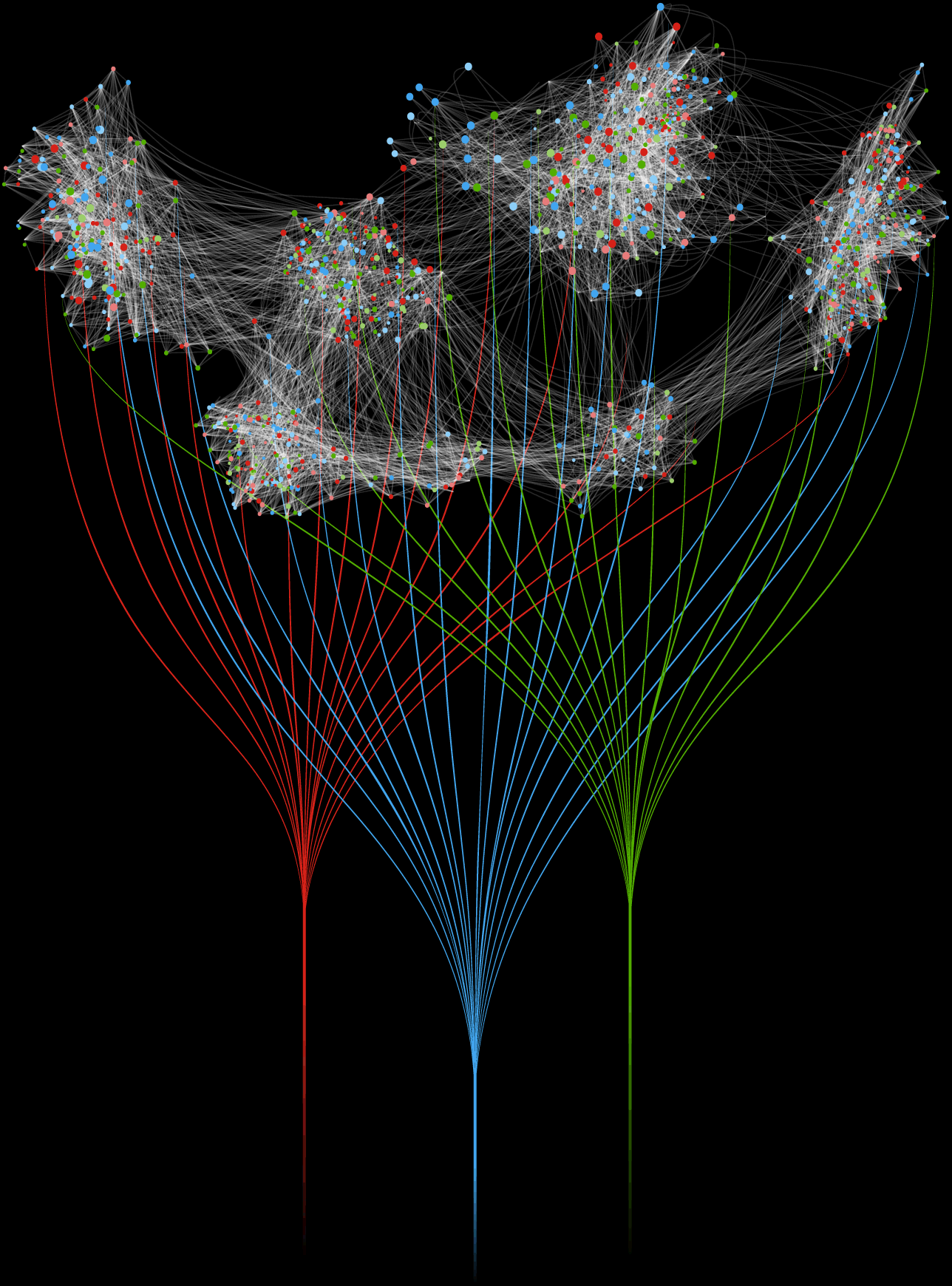
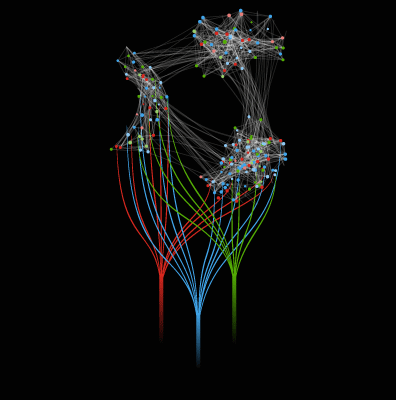
Aceiss gives you insight into how access is structured across your company.
Automate the integration of legacy and new applications, and light up your control systems.
Immediately identify anomalous behavior and toxic combinations. Manage user permissions. Monitor and protect user accounts.
See patterns of access you didn’t even know existed.
Be confident in your security.
Automate integration of your existing applications and security infrastructure, and begin delivering insights immediately.
Whether it’s one application or thousands, Aceiss makes security possible for you.
20 applications
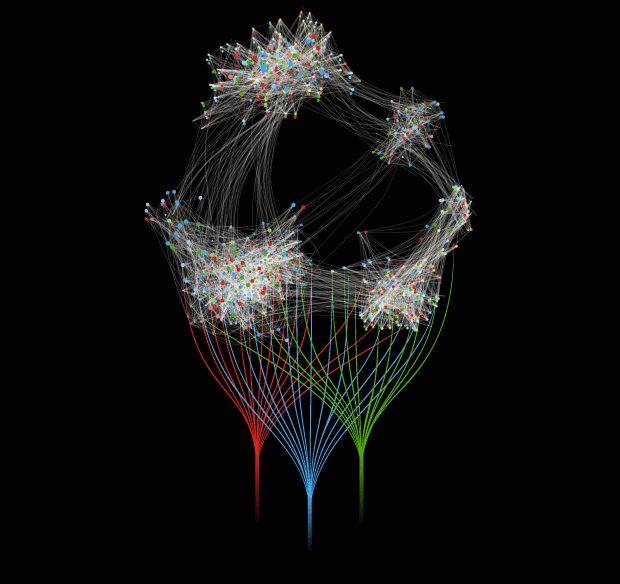
200 applications
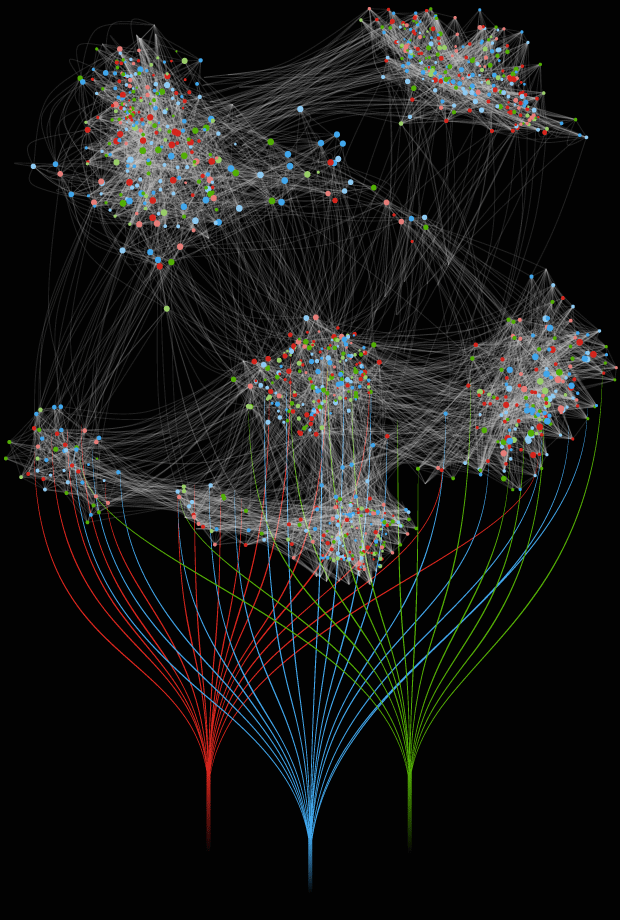
5,000 applications with extensive legacy systems
Rapidly move seamlessly from undocumented applications to specific signals that describe who has access to what.
Aceiss uniquely makes sense of user access in real-time across the entire application estate and correlates this with activity to detect anomalous behavior.
See how permissions are organized across your company and manage user roles your way.
Dramatically reduce the time to achieve and prove compliance. Make your auditors happy.
Verify. Contextualize. Grant least privilege.
Aceiss compliments your existing security ecosystem and makes it stronger.
Aceiss is fast, easy, and efficient, dramatically reducing the time and money required to gain visibility across all user access and application activity.
Our pricing is based on the number of applications empowering you to efficiently secure your data while keeping costs down and avoid regulatory hassle.
The risk of unauthorized access is a real and growing threat for everyone.
Aceiss empowers access security, providing unprecedented visibility and insights into user access.
Aceiss helps make the world a safer place.