You can’t protect what you can’t see.
Aceiss protects against cyber attacks by revealing unauthorized use of employee access to company systems. Don’t let attackers exploit unknown vulnerabilities to breach security.

Aceiss protects against cyber attacks by revealing unauthorized use of employee access to company systems. Don’t let attackers exploit unknown vulnerabilities to breach security.

Advancing Zero Trust Maturity Throughout the Visibility and Analytics Pillar
Aceiss for GitHub helps identify and eliminate unusual user access across GitHub repositories. It is the is the first line of defense for CISOs and risk managers against security threats.

Aceiss employs automation to meet the stringent requirements of the NSA for the optimal implementation of state-of-the-art zero trust environments.

Install a simple agent to gain immediate access to an application’s user accounts, permissions, and activity.
Highlight patterns of unauthorized access, anomalous behavior, and dangerous combinations of user privileges.

Integrate with existing access control systems for lasting protection and maximum return on investment.
Monitor all activity in real time, identify access privileges across the organization, and determine appropriateness.

Conduct compliance and governance tasks, as well as access reviews and audits.
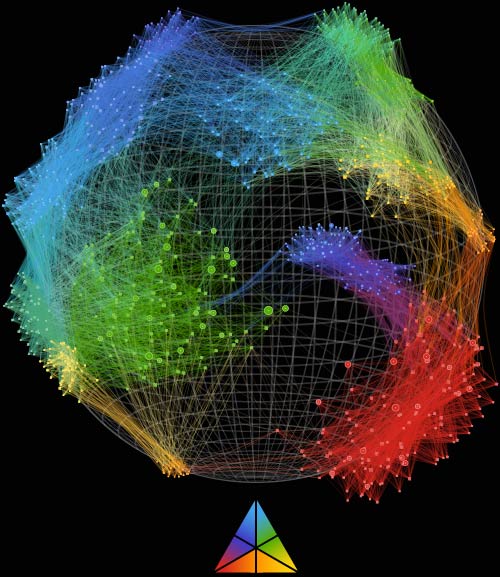
The threat of unauthorized access is a genuine and escalating concern for everyone.
Aceiss empowers access security, offering unparalleled visibility and insights into user access.
Aceiss makes the world a safer place.